1. Introduction
Cloud computing is a combination of different configurable computing resources like networks, servers, storages, services, applications that help in providing convenient and on-demand access to the cloud users [1]. Cloud computing is largely mentioned by people and is currently used in many commercial fields. Cloud service providers (CSPs) are responsible for identity and other kinds of management in cloud environment. However, a large number of data leakage incidents are caused due to the vulnerabilities in identity management systems [2]. Identity and access management (IAM) in cloud environment is a crucial concern for the acceptance of cloud-based services. Presently, the mechanism of identity management is mainly CSP-centered, which hardly meets the requirement of users’ flexible and fine-grained access control policy.
The cloud environment is generally classified as Private Cloud, Public Cloud and Hybrid/Federated Clouds. A private cloud is designed and dedicated to the needs of a specific organization. In a public cloud environment, infrastructure support to multiple organizations is facilitated and managed by third party provider. Public cloud model is also known as multi-tenant environment which shares the resources among the organizations to bring down the overall service cost. Hybrid or Federated cloud infrastructure is a mix of on-premises, private and public cloud services. Another concept in cloud infrastructure is multi-provider clouds which is an environment that relies on multiple clouds providers and divides the work load among the cloud environment. There are also different cloud environments which is specifically designed to support the service like Internet of Things (IoT) cloud services which are specifically designed to handle and analyse the data from IoT devices and mobile cloud services which uses cloud computing to deliver applications to mobile devices.
Cloud computing is commonly divided into three primary cloud service models, such as Software-as-a-Service (SaaS), Platform-as-a-Service (PaaS), and Infrastructure-as-a-Service (IaaS). Cloud is based on service-oriented architecture which has the capability of providing Database-as-a-service (DbaaS), Identity-as-a-service (IDaaS) and Anything-as-a-Service (XaaS) [3]. Cloud computing provides a better way of handling resources in both industry and academia. Cloud system is vibrant in nature by considering numerous users, devices, networks, organizations, and resources that are frequently connected and disconnected to the system. The best option for the cloud service model that has to be implemented is determined through a number of factors. The important factors that are to be considered are flexibility, scalability, interoperability, and control of service [4]. Cloud computing requires extensive authentication and authorization mechanism to secure its data and resources due to the complexity of usage. Lack of efficient mechanism creates multiple challenges in cloud environment which include identity management, risk management, trust management, compliance, data security, privacy, transparency, and data leakage [5]. Another facet of cloud systems is complexity and their associated security challenges. The loss of control and transparency issues are also created while storing and processing user information by Cloud Service Providers (CSPs), or outside the organizational boundaries. Due to these distinctive security challenges, the cloud environment adoption is slow regardless of the assured and attractive features of the cloud. In spite of the aforesaid problems, the organization has a tendency of reluctance in contributing their critical identity information to the cloud [6].
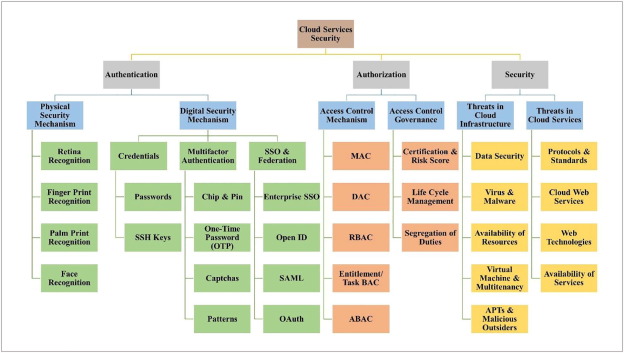
In a cloud system, the storage and processing of data is performed by organizations or with the help of third party vendors. The service provider has to ensure that data and applications stored in cloud are protected as well as the infrastructure is in secure environment. Further, users need to verify that their credentials for authentication is secure [7]. There are many security issues that compromise data in the process of data access and storage in the cloud environment, especially in the case of data storage with the help of third party vendors who themselves may be a malicious attacker. Though standards and best practices are available for overcoming such security problems, cloud service providers are reluctant in securing their network with the updated set of security standards [8]. Identity and access management is one of the best practices to measure on cloud services. Presently, Identity and Access Management (IAM) provides effective security for cloud systems. IAM systems perform different operations for providing security in the cloud environment that include authentication, authorization, and provisioning of storage and verification. IAM system guarantees security of identities and attributes of cloud users by ensuring that the right persons are allowed in the cloud systems. IAM systems also help to manage access rights by checking if the right person with the right privileges are accessing information that are stored in cloud systems [9]. Currently, many organizations use Identity and Access Management systems to provide more security for sensitive information that are stored in the cloud environment. A taxonomy of cloud services security is shown as Fig. 1.
 Fig. 1. Taxonomy of cloud services security.
Fig. 1. Taxonomy of cloud services security.The major contributions of the paper are summarized as follows:
-
-
Comparative analysis of different aspects in identity and access management mechanisms in cloud environment.
-
-
Overview of access governance policies which are least explored area in identity and access governance.
-
-
Overview of market leading identity and access control suite of products and solutions.
-
-
Overview of common security threats in Cloud IAM systems and prevention techniques.
-
-
Recommendations on governance policies and industry best practices.
Further, the rest of the paper is organized in eight sections. The authentication mechanisms that include credentials, SSO and federation are dealt in Section 2. Section 3 deals with access control mechanisms, access control policies and access control delegation. Identity and access management systems are analysed in Section 4. The security threats in cloud computing that include, data security, Virtual Machine (VM) and multi-tenancy are detailed in Section 5. Analysis of security threats in cloud environment is presented in Section 6. Recommendations and industry best practice are discussed in Section 7. The survey is concluded in Section 8.
2. Authentication mechanisms
Authentication is the process of approving an entity through another entity. It is used to ensure whether the person or the application is eligible for accessing or claiming. The authentication process is usually performed by a software or by part of a software [10]. The common authentication methods in a network environment are log-on credentials, multifactor authentication, third-party authentication, simple text passwords, 3D password objects, graphical passwords, biometric authentication and digital device authentication. A cloud system follows any one or combination of the aforesaid authentication mechanisms [11]. Presently, cloud access permission is granted through an identity management system.
2.1. Physical security mechanisms
Physical security mechanisms like, access cards and biometrics ensure security of cloud resources and facilities by denying unauthorized access through authentication. Cloud data centers (CDCs) are the recent attractions of organizations as they provide ease of access to their customers at any time. CDCs centralize all servers, networks and applications so that users access data at any time and from any location. As a part of data center security, access cards and biometric authentication like, iris or retina recognition, fingerprint recognition, face recognition and palm print recognition can be used. In order to prevent the data leakage from insiders or any unauthorized access to data centers, physical security along with certain usage and governance policies are required. Physical security mechanisms presently used are biometric access control and digital devices for authentication [12].
2.2. Digital security mechanisms
2.2.1. Credentials and secure Shell keys
Credentials are the evidence of authority, status, access rights and entitlements. It gives the evidence that the particular user is entitled or deserves to utilize resources and services. The usage of credentials like one-time password, pattern, and captcha is a traditional way of securing the system from malicious activities. Most commonly used mechanisms to manage access credentials for cloud environment are Lightweight Directory Access Protocol (LDAP) and Microsoft Active Directory (AD) technologies. LDAP and AD servers are managed by either third party vendors or within the organizational network in cloud computing [13]. Cloud maintenance overhead increases when multiple applications are deployed on these traditional credential management mechanisms. It is essential to add, disable, modify or remove accounts whenever any employee leaves or enters the organization. In managing the credentials at the provider side, weak credential reset vulnerability is represented when weak password recovery mechanisms are used. The hackers can monitor or manipulate data in the cloud along with malicious redirects whenever the credentials are compromised [14].
Secure Shell (SSH) keys help to identify the SSH server through public-key cryptography or challenge-response authentication. The main advantage of SSH keys is that the authentication to the server is performed without passing the password over the network. This prevents the interception or cracking of the password by hackers. The attempts of guessing credentials through brute force attacks during authentication are eliminated by SSH keys. SSH agents help to establish connection with servers without using separate passwords for each system. SSH key agent stores the private keys and provide them to the SSH client programs. These private keys are encrypted with passphrase and the passphrases are provided during each attempt to connect with the server. In every individual invocation of SSH, the passphrases are needed to decrypt the private key before proceeding to authentication phase. The passphrase is utilized only during the process of adding the private keys to the agent’s store. This attempt favours the communicating devices which makes frequent SSH connections. SSH agent runs automatically once the login is initiated and persists for the entire session duration. The main concern of SSH keys is that the security is not better than credentials if the private keys are not well protected. Static credentials and SSH key mechanisms are commonly used for cloud web service authentication.
2.2.2. Multifactor authentication
Multifactor authentication is another method to secure digital assets and transactions over the Internet. Typically, One-Time Password (OTP), Captchas or Patterns are used as the secondary authentication mechanism along with credentials. Multifactor provides additional layer of security over the traditional credential based authentication. Generally, online transactions are authenticated using One-Time Passwords. In the financial transactions through online, server generates a one-time password using specific algorithms based on its configuration and the generated OTP is sent to the user either through a registered mobile number or through email. Another type of OTP is generated with the help of hardware/software token generators which is protected by a Personal Identification Number (PIN). This password can be used once and it has a certain time limit for usage. Captcha is normally used to secure the web applications from attacks by programmatically driven malware. Captcha could be an alphanumeric combination, a mathematical equation or an image and with a provision for a refresh. Patterns are another form of authentication which has different formats. Dotted patterns are widely used in mobile applications while matching image selection is predominantly used in web applications. The usage of security questions is an alternate method of securing digital assets which is a form of shared secret. In this method, the user selects security questions from the predefined list and defines the answer. At the time of authentication, the predefined security questions appear on the login screen and by providing the defined answer along with the credentials allow the user to get authenticated.
2.2.3. Chip & PIN
Chip and Personal Identification Number (PIN) is the conventional method of authentication for financial transactions. This can also be used for authentication to machines/services in a network of an organization. The asymmetric encryption technology uses public and private keys to encrypt and decrypt data used in the chip & PIN mechanism. The microprocessor chip stores the user data and security keys through the creation of unique transaction data to protect against frauds. The communication between the client/terminal with the authentication server is encrypted and signed with the help of security key which is stored in the chip. The server verifies the signature and decrypts the communication with the help of pairing keys which are stored in the server. The PIN is used to authenticate the client/terminal for accessing the user data and keys from the chip.
2.3. SSO & federation
The conventional authentication mechanisms are not always applicable for remote authentication. Authentication for accessing SaaS application needs centralized monitoring to limit software piracy. Multiple services are most likely to be subscribed by the cloud customers, resulting in multiple login requirements [15]. It also creates problem in maintaining a large number of credentials by a single user. The possible solution is the usage of single sign-on techniques. Single Sign-On (SSO) provision helps the cloud users to use one password for all application/service access. It provides secured and uninterrupted services by keeping one credential for each user. The users need not specify their credentials at every time of accessing different cloud web services [16]. Security Assertion Markup Language (SAML), Open Authentication (OAuth) and OpenID provide Single Sign-On (SSO) facility by allowing the Identity Provider (IdP) to share the authentication and authorization information with the Service Providers (SPs) as shown in Fig. 2.
 Fig. 2. Comparison of different authentication mechanisms in cloud environment.
Fig. 2. Comparison of different authentication mechanisms in cloud environment.2.3.1. Enterprise SSO
Enterprise Single Sign-On facilitates the storage and transmission of user credentials with the help of encrypted session cookies across web based applications. Once a user is authenticated through a centralized authentication server, SSO generates a browser based encrypted session cookie. While the user navigates from one application to another, the new application checks for a valid session cookie. The user details are read from the valid session cookie and the user is authenticated to the targeted application. Whenever any application is not able to find a valid session, the user is navigated to the centralized authentication mechanism for re-authentication. A new session will be generated for the target application after successful authentication.
2.3.2. OpenID
OpenID is an open standard authentication protocol which allows the user’s authentication to the relying parties (RP) with the help of third party identity vendors. A relying party (RP) is a resource provider which could be a website or application that requires the end-user verification. OpenID supports SSO services by allowing single credentials for authenticating to multiple websites and web service accesses. There is no need for the usage of webmasters in OpenID system as it supports decentralized authentication mechanism. OpenID identity provider stores the list of users and with the help of identity provider’s list, users create their accounts. The cloud users login into any website which supports OpenID authentication by using their accounts. The latest version of OpenID protocol is OpenID Connect (OIDC) which is built on the top of the OAuth protocol. OpenID Connect supports authentication mechanisms for native and mobile applications. It also provides an option for encrypting and signing the communications between the participants.
2.3.3. OAuth
An alternative method of authentication mechanism is OAuth which offers one-way authentication or mutual authentication for cloud computing [17]. OAuth is an open standard for access delegation which grants access to the user on other website/application without sharing the passwords from an authenticated website/application. The current version of OAuth protocol is OAuth 2.0. The relying parties (RP) need to register with the OAuth token provider to obtain client identifiers and client secrets. When an end user tries to access the relying party, it will be redirected to the identity provider for authentication. Once the user is successfully authenticated, the identity provider shares the OAuth accesstoken along with refresh token, client id and the client secret. The relaying party retrieves the additional user details from the user info end point. The relaying party renews the access token during its expiry with the help of refresh token. The digital signature for the access tokens is not promoted by OAuth2.0.
2.3.4. SAML
Security Assertion Markup Language (SAML) basically works on token-based request and response techniques and it is also an open standard mechanism for communicating between two parties [18]. These two parties are particularly service provider (target application) and identity provider. SAML ensures the authentication of users with target application is secured. SAML tokens do not contain any user credential information. SAML also allows to encrypt and encode data communication between the identity provider and service provider (target application). It ensures that the user is securely authenticated to the target application [19]. SAML provides web browser single sign-on (SSO) and promotes interoperability by specifying and standardizing the web browser SSO profile. The SAML specification involves the roles of user, identity provider and service provider. When a user request for a web service from target application, the target application requests and gets authentication assertions from identity provider. The target application takes decision about the access rights based on the assertion. The social networks use SAML exchanges for providing identity services. Table 1 summarizes the various authentication mechanisms and their associated security issues.
Table 1. Summary of Various Authentication Mechanisms - Security Aspects and Issues.
| Topic | Mechanisms | Security Aspects | Issues/Attacks | Reference |
|---|---|---|---|---|
| Physical Access | Centralized data storage | Physical presence is mandatory and verified using access card or biometrics | Malicious Insiders, Cool Boot Attack | [4], [5], [12], [13] |
| Credentials | Lightweight Directory Access Protocol (LDAP), Connectors, Database Storage and Microsoft Active Directory (AD) | Individual access rights per application | Weak credential-reset vulnerability, Phishing and malicious redirects | [5], [13], [15], [17], [18], [19], [22], [37], [78] |
| Multifactor | One Time Password, Tokens & Biometrics | Additional authentication layer over the credentials | DoS Attack, Replay Attack, Phishing Attack and Identity Theft | [11], [13], [14], [67], [74] |
| Single Sign-On | SAML, OpenID, OAuth |
Single password for all the associated applications Centralized password policies No password sharing to applications |
Cross Site Request Forgery, Replay Attack, Cross Site Scripting | [13], [15], [16], [18], [19], [69] |
3. Authorization mechanisms
Authorization is the method of permitting or disagreeing access to a particular resource depending on an authenticated user’s entitlements. The authorization process decides which user or what applications are allowed to perform on the system and user/application identity information are used for pleasing the decision [20]. Cloud network contains different service providers’ environment in which a single user is able to access different kinds of services at the same time while each service is from a different service provider and with different security levels. Sometimes, authorization rights are given by third-party vendors and these third-party applications are authorized to access certain private information as shown in Fig. 3. Such permissions are unsafe since the privacy of the user is involved. For example, in social networks, cloud-based hosted applications are accessed by outside applications whenever the user authorizes that application [21]. In case of malicious activity, it is easier to obtain intelligence on targets. Authorization in a cloud environment is attained by either access control policies or access right delegations. The CSP defines and implements access control policies such that the resources and services are accessed only by the authorized users. Centralized access control mechanisms are advantageous to the organizations in securing sensitive information, reducing several management and security tasks [22].
 Fig. 3. Comparison of different Access Control Mechanisms in a cloud environment.
Fig. 3. Comparison of different Access Control Mechanisms in a cloud environment.3.1. Access control mechanisms
3.1.1. Mandatory access control
Mandatory access control (MAC) mechanism is the traditional mechanism to define the access rights of users. MAC gives access permission through the operating system or security kernel. It controls the ability of data owners to grant or deny access rights to clients for the file system. All access control rights are set by the system manager and imposed by the security kernel or operating system. Clients have no rights to alter these access rights. In mandatory access control model, each file system object has a classification label such as, secret, top secret or confidential level. Each device and client is assigned a similar classification and clearance level. The security kernel determines the classification label of clients and resources. The operating system or security kernel checks the credentials of each person or system while accessing a particular resource to determine the access rights of that specific person or device. Even though MAC provides more security in accessing the resources, it needs careful planning and frequent monitoring to keep all the classification labels up-to-date [23]. MAC has less flexible environment to process the access rights.
3.1.2. Discretionary access control
Discretionary access control (DAC) is a security access control mechanism which controls the access permissions through data owner. In DAC, the access rights of each user are performed during authentication by validating the username and password. DACs are discretionary as owner determines the privileges of access. In DAC, file or data has owner and the data access policies are controlled by data owner [24]. DAC provides more flexibility than MAC however, DAC provides less security than MAC. Table 2 summarizes the various authorization mechanisms and their associated security issues in cloud environment.
Table 2. Summary of Various Authorization Mechanisms - Security Aspects and Issues.
| Topic | Mechanism | Security Aspects | Issues/Attacks | References |
|---|---|---|---|---|
| Access Control | MAC | Application owns the individual access permissions | Unauthorized access, over classification of data, difficult to implement, | [15], [20], [23], [24], [25], [26], [42] |
| DAC | Access rights to an application is owned and controlled by another application | Trojan horse susceptibility, Flawed software, Information flaws, Malicious attacks | ||
| RBAC | Access rights and privileges to multiple applications are bundled as an organizational role | Administrative issues, data abstraction issues, Real-time issues | [15], [24], [25], [26], [28], [32], [36], [37], [42] | |
| ABAC | Access rights and privileges to an application determined based on Subject, Object, Policy and Environmental Attributes | Delegation issues, administration issues, auditability and scalability issues |
3.1.3. Entitlement/Task based access control
Entitlement or task based access control is one of the minute level access control mechanism. A specific access permission is required for each task, action or process that is represented by an entitlement or task. This model has capabilities to handle complex access conditions to determine whether the access rights need to be granted or denied. The major concern about entitlement access control model is the maintenance of large number of entitlement sets. The users also need to raise separate request and get the approval for each entitlement. Entitlement or the task based access control model has the ability to represent and implement other hierarchical access control models like role-based access control and attribute based access control.
3.1.4. Role based access control
Role Based Access Control (RBAC) provides access rights based on roles and privileges of the users. User permissions are given by different parameters of RBAC like, user-roles, role permissions and role-role relationships. The roles are classified into two categories as application/technical role and organizational/business role. An application/technical role contains the combination of different application specific entitlements or tasks based permissions and its scope is limited to the specific application. An organizational/business role is generated based on different job functions and access rights assigned to an employee [25]. An organizational/business role is a combination of different application/technical roles. RBAC provides administration security in organizations with large number of users and number of permissions. RBAC contains mainly three rules for assigning permission to a particular user, such as, role assignment, role authorization and permission authorization. The permissions for accessing the data are provided to users based on these rules. RBAC provides a highly secured environment for assigning access permissions. The main limitation of RBAC is that the assigned roles may change from time to time which needs a real-time environment to check and validate the changes.
3.1.5. Attribute based access control
Attribute-based Access Control (ABAC) is a mechanism to control the access permissions. ABAC defines the access control mechanism by the use of policies which determines different sets of attributes to check the access rights of each user. The policies are generated using different types of attributes and based on the policies, the system determines the access permissions. The considered attributes are subject attributes, object attributes, resource attributes and environmental attributes. In the ABAC model, roles and privileges of each user are pre-defined. It resolves many authorization problems, achieves an efficient regulatory compliance and allows flexibility in implementation [26].
3.2. Access control governance
Cloud service providers define policies related to access control in IAM system for ensuring only the valid users are accessing the resources and services. In order to achieve the objectives of each organization, CSPs have to ensure three important characteristics namely, Governance, Risk Management and Compliance (GRC) [27]. Governance is the process of organizations which reflect the complete organizational structure and management mechanisms to achieve their goals. These governance policies are defined and executed by the board of directors of that particular organization. GRC mechanism tries to implement the synchronization of sensitive information and the activities across governance, risk management, compliance for improving the efficiency of operation, effective resource sharing, wasteful overlaps and efficiency of report activities in organizations. Risk management is the process of managing risks associated with resource sharing and access permissions to achieve the objectives of organization. Compliance refers to the offering of organizational policies, laws, regulations, and procedures [28].
3.2.1. Certification & risk score
Certification is the process of verifying the links between users, roles and resources to ensure that they are true and correct. Certification enables to review the role hierarchy, user privileges and business rules that are defined in Identity Governance. When a certification is initiated, IAM system automatically invites managers to review and certify the access privileges of the users or resources under their administration. User certification is provided to certify the resources and roles associated with a user. Generally, the privileges of employees are reviewed by the managers. The resources, parent roles, child roles and users linked to each role are certified using role certification. Resource certifications are used to certify the resources and users who are linked to each resource. The roles associated with users are reviewed by administrators of each resource and the access rights of each user with resources are validated. Account certifications are used to certify each account that are linked to users. Each account and its user assignments are typically reviewed by the compliance officer. When a user certifies his own privileges, it is called self-attestation certification. Risk scores are derived based on threat indicators from identity, accounts and entitlements, assets and behavior context. These risk scores are certified by risk score based certification. The user-centric risk score triggers risk-based access certification system. The end result in access certifications provide the most effective, efficient access governance and administration processes.
3.2.2. Life cycle management
Life cycle management is the process by which the process of creation or deletion of accounts, management of accounts, entitlement changes and track policy compliance are performed. The lifecycle management of an individual’s identity allows to securely enable access to the right applications. In lifecycle management, user is managed starting from the point of granted access throughout his lifecycle which includes, change of role, entitlement and removal at a point where the relationship concludes.
3.2.3. Segregation of duties
A proper segregation of duties is one of the audit objectives in the organizational framework. Basically, two or more stages of transaction/operation should be controlled by more than one person as per segregation of duties. Organizations need to define the right policies to ensure responsibility assignments and cross checking of duties. Segregation of duty mechanism helps to prevent deliberate frauds as it requires the involvement of two or more people. It also helps in finding out the innocent errors which happens in the process work flow. The duties or responsibilities are broadly classified into four categories, namely, authorization, record keeping, custody and reconciliation. The review and approval of transactions or operations happens in the authorization phase. Record keeping is the phase of creating and maintaining the logs. The custody is the phase of having access or control over a physical or digital asset. Finally, the verification and recording of transactions happens in reconciliation phase. Table 3 summarizes the various access control mechanisms and their associated security issues in cloud environment
Table 3. Summary of Various Governance Mechanisms - Security Aspects and Issues.
| Topic | Mechanism | Security Aspects | Issues/Attacks | References |
|---|---|---|---|---|
| Access Control Policies | Governance | Periodic identity and access certification | Cyber-attacks, data and security breaches, transparency issues, segregation of duties | [25], [26], [29], [39], [41], [63], [64], [65], [66], [68] |
| Risk Management | Risk score calculation, Preventive mechanisms | Data Tampering Attack, Elevation of Privilege & Spoofing Attack | ||
| Compliance | Organizational policies and implementation | Phishing attacks, loss of control | ||
| Identity and Access management | Credential Synchronization, provisioning & Identity Federation | Right Person, Right Access, Right Resource at Right Time | Synchronization leakage, Identity Theft, Data Tampering Attack & Spoofing Attack | [9], [10], [19], [30], [31], [70] |